Detect and stop insider attacks with Data Intelligence
17 August 2021

This article is part of Certis' Insights Series that feature the latest Artificial Intelligence applications and developments.
Download links for the Certis research paper(s) mentioned in this article can be found at the end of the page.
The Rise of Insider Attacks
COVID-19 has upend-ed the way organisations conduct their businesses and employees utilise office premises.
With the under-utilisation of premises and reduction of the resources used to maintain and oversee internal operations, there is a likelihood of increased security risks.
Physical access control, including employee / guest access and management systems, supervised doors / locations and surveillance cameras are critical checkpoints of a premise in terms of security monitoring.
Besides looking for external threats , there is also the current problem of insider attacks that organisations often neglect or overlook due to lack of awareness and budget:

Full Time and Contract Employees, Contractors
Insider attacks by holders of legitimate access cards tries to access unauthorised areas

False Credentials
Access through social engineering or theft of access cards
Operationalising Data Intelligence to Enhance Premise Security
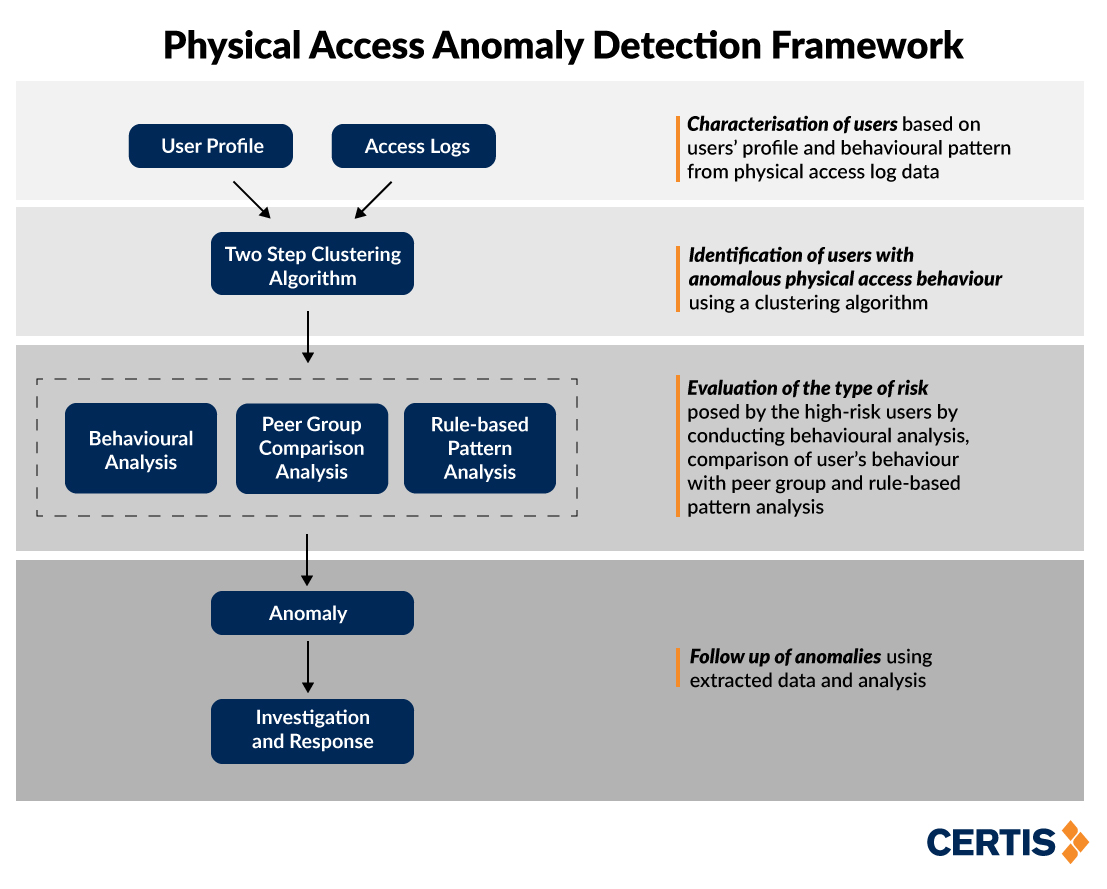
To help organisations detect and stop insider attacks effectively and efficiently, Certis’ researchers developed a propriety method called the Physical Access Anomaly Detection Framework that uses an unsupervised machine learning algorithm known as the Two Step Clustering method.

Two Step clustering is scalable and do not require predefined rules or patterns
Published in the paper "Physical Access Log Analysis: An Unsupervised Clustering Approach for Anomaly Detection” by Certis, the method characterises users based on their physical movement behaviours and job profiles in order to identify users with anomalous physical access behaviours within a premise.
It does not need any predefined rules or patterns, is able to consider both categorical and continuous data, and has high scalability, which is required for near real-time anomaly detection.
Certis is also exploring how such anomaly detection can be further enhanced with deep learning methodology.
Benefits for Your Organisation
Automated detection of security anomalies
 Enhanced security for your premises
Enhanced security for your premises
Integrated orchestration of building operations
Industries that will Benefit from this Solution
Government
 Retail and Building Owners
Retail and Building Owners

Commercial Property Owners
To download the research paper "Physical Access Log Analysis: An Unsupervised Clustering Approach for Anomaly Detection" published by Certis - click here
Tagged Topics: